

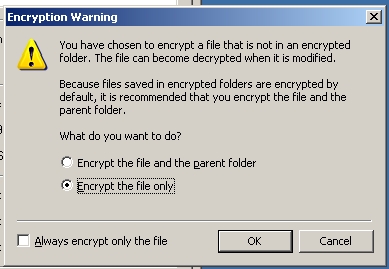
The Encrypting File System (EFS) on Microsoft Windows is a file system filter that provides filesystem-level encryption and was introduced in version 3.0 of NTFS[1]. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.I encountered a problem while trying to do this practical.
Operation
EFS works by encrypting a file with a bulk symmetric key, also known as the File Encryption Key, or FEK. It uses a symmetric encryption algorithm because it takes a smaller amount of time to encrypt and decrypt large amounts of data than if an asymmetric key cipher is used. The symmetric encryption algorithm used will vary depending on the version and configuration of the operating system; see Algorithms used by operating system version below. The FEK (the symmetric key that is used to encrypt the file) is then encrypted with a public key that is associated with the user who encrypted the file, and this encrypted FEK is stored in the $EFS alternate data stream of the encrypted file.[citation needed] To decrypt the file, the EFS component driver uses the private key that matches the EFS digital certificate (used to encrypt the file) to decrypt the symmetric key that is stored in the $EFS stream. The EFS component driver then uses the symmetric key to decrypt the file. Because the encryption & decryption operations are performed at a layer below NTFS, it is transparent to the user and all their applications.
Folders whose contents are to be encrypted by the file system are marked with an encryption attribute. The EFS component driver treats this encryption attribute in a way that is analogous to the inheritance of file permissions in NTFS: if a folder is marked for encryption, then by default all files and subfolders that are created under the folder are also encrypted. When encrypted files are moved within an NTFS volume, the files remain encrypted. However, there are a number of occasions in which the file could be decrypted without the user explicitly asking Windows to do so.
Files and folders are decrypted before being copied to a volume formatted with another file system, like FAT32. Finally, when encrypted files are copied over the network using the SMB/CIFS protocol, the files are decrypted before they are sent over the network.
The most significant way of preventing the decryption-on-copy is using backup applications that are aware of the "Raw" APIs. Backup applications that have implemented these Raw APIs will simply copy the encrypted file stream and the $EFS alternate data stream as a single file. In other words, the files are "copied" (e.g. into the backup file) in encrypted form, and are not decrypted during backup.
Starting with Windows Vista, a user's private key can be stored on a smart card; Data Recovery Agent (DRA) keys can also be stored on a smart card.
Source:Wikipedia

Vista Home basic and premium do not deliver the capability to encrypt but just to decrypt folders and files.
Encrypting File System Supported operating systems
Windows
- Windows 2000 Professional, Server, Advanced Server and Datacenter editions
- Windows XP Professional, also in Tablet PC Edition, Media Center Edition and x64 Edition
- Windows Server 2003 and Windows Server 2003 R2, in both x86 and x64 editions
- Windows Vista Business, Enterprise and Ultimate editions[6]
- Windows 7 Professional, Enterprise and Ultimate editions
- Windows Server 2008 and Windows Server 2008 R2
- Source: Wikipedia



Labels: Hands-on Project, Practical08
林小颍's work ^—^V